An important part of incident response is still an analytical process to understand the cause of an incident and select response actions. Using therefore visualisations in security operation centres (SOC) can improve the alert triage of analysts by visual analytics to handle tons of alerts each day. Such an analysis requires a good understanding of cyber attacks and experiences to detect suspicious patterns in visualisations. However, this analytical process happens in the mind of analysts and cannot easily be transferred to others. Understanding the reasons for user insights and their manner is most relevant and challenging for analytical provenance.
In SAPPAN we have researched on analytical provenance in visualisations to make such an analysis comprehensible. Similar to data provenance that captures the traceability information about where data comes from and how the data was manipulated over time, we capture information about the visualised data and interactions applied in visualisations. To expand the SOC analysts’ opportunities within the SAPPAN dashboard, we created a tool to record interactions and use the recorded data to visualise the sequence of user activities.
This approach allows analysis sessions to be interpreted and understood by both humans and machines, making them comparable and suitable for various applications.
The figure below shows in a graphical interface a recorded sequence of interactions. The lanes show different sources of interactions like the visualisations used for analysis or the comment box to annotate insights. Between a start and end circle, the rectangles called Task show that different filters have applied to the data to manipulate the representation. To gain further insight into the analysis, a user can click on the rectangles to see what the visual representation in the dashboard looked like at the time of recording.
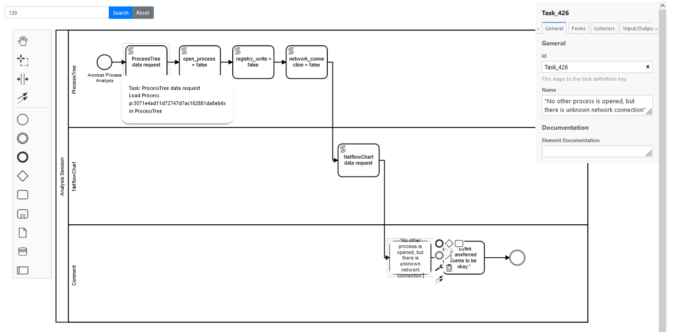
With that approach, a user can recap the interactions that lead to an analysis result, share it or use it to improve processes where necessary. If analytical provenance is thought of even further, recommendations for handling can be derived from it and clustered for specific attacks. With that, a SOC can compare their analysis sessions and use them to a shared knowledge base in malware analysis.