By Tomas Jirsik (Institute of Computer Science, Masaryk University)
Network traffic monitoring is a rich source of information on host behavior. The passive large-scale approaches to traffic monitoring, such as network flow monitoring [1], enable us to observe a behavior of a large number of hosts in a network without the necessity to have direct access to these hosts. Current network monitoring approaches can provide information on each connection, even in high-speed networks, without any sampling.
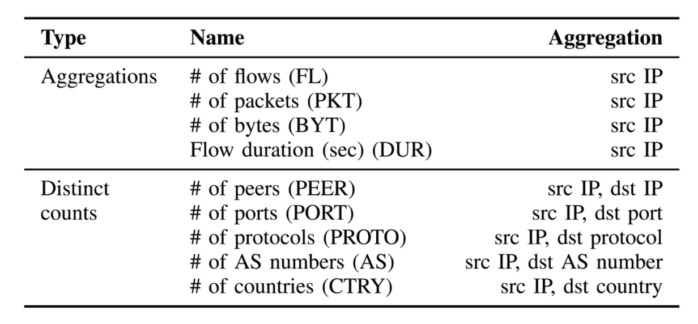
The data retrieved by network monitoring tools from network traffic represents individual connections (either one- or bi-directional). However, these network connections need to be transformed into features properly embedding the hosts behavior. Table 1 presents the basic features that can be extracted from the network connection records provided by a majority of the network monitoring tools.
The models of host behavior can capture various aspects of host behavior. A commonly modeled behavior element includes temporal characteristics of the behavior, volumetric nature of the behavior, and last but not least, the usual habits of a user such as frequently visited domains, AS, or countries. More advanced analyses of the host behavior can focus on the identification of the stability of the host behavior, anomaly detection, behavior change detection, or host clustering.
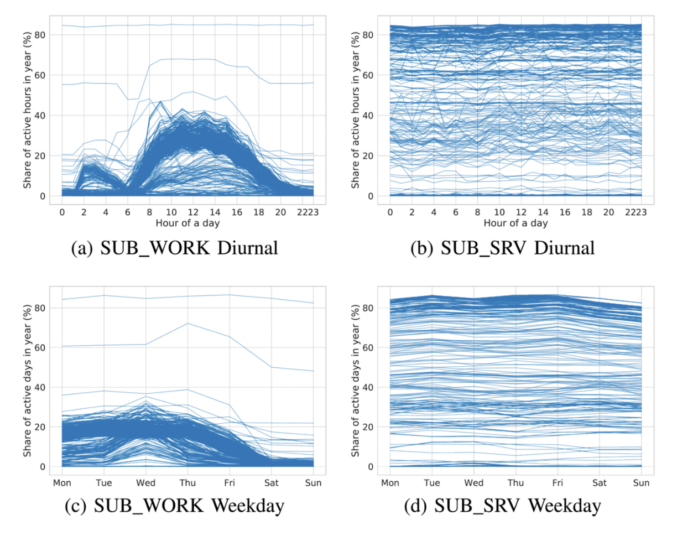
Figure 1 provides an example of the analysis of active communication times for hosts in different types of subnets in a network over a year. A line in the figure represents a share of a single host’s active observations in a year. The diurnal pattern with the peak at noon and a smaller peak at 3 AM are present in the segment containing mainly work stations of regular workers (SUB_WORK). The peak culminating at noon represents the typical daylight activity. The smaller peak at 3 AM is caused by the updates of the workstations planned by the central management system. Similarly, the weekday pattern is observable at the SUB_WORK, which reflects the fact that the majority of the hosts in the SUB_WORK subnets are used by the employees of the university. Hosts in the server segment (SUB_SERV), on the other hand, do not show any significant diurnal pattern.
Modeling the stability of the host behavior aims to identify hosts with unstable (i.e., irregular, more random) and differentiate them from the hosts that behave consistently in time. We can then work with the assumption that the hosts with consistent behavior in time usually pose a lower risk and do not be monitored in greater detail compared to the hosts with inconsistent behavior. The figures below present selected use-cases that can be identified using the host behavior models derived from their network behavior.
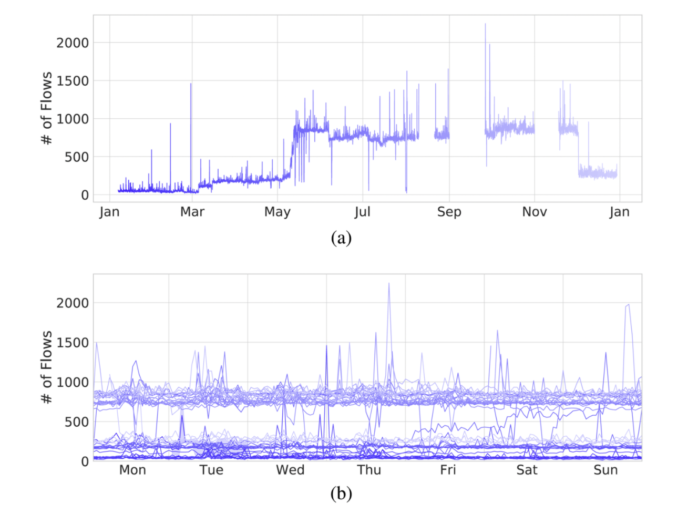
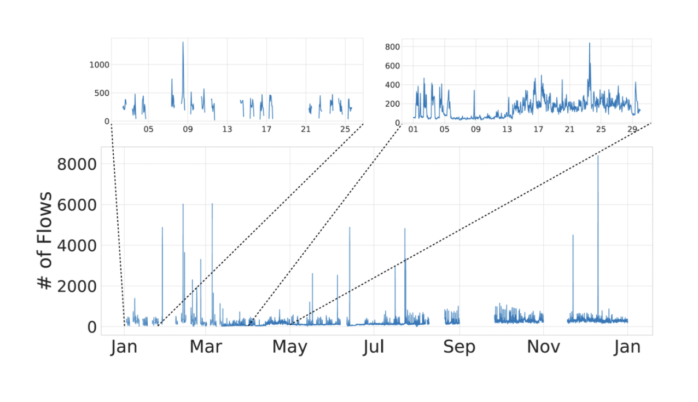
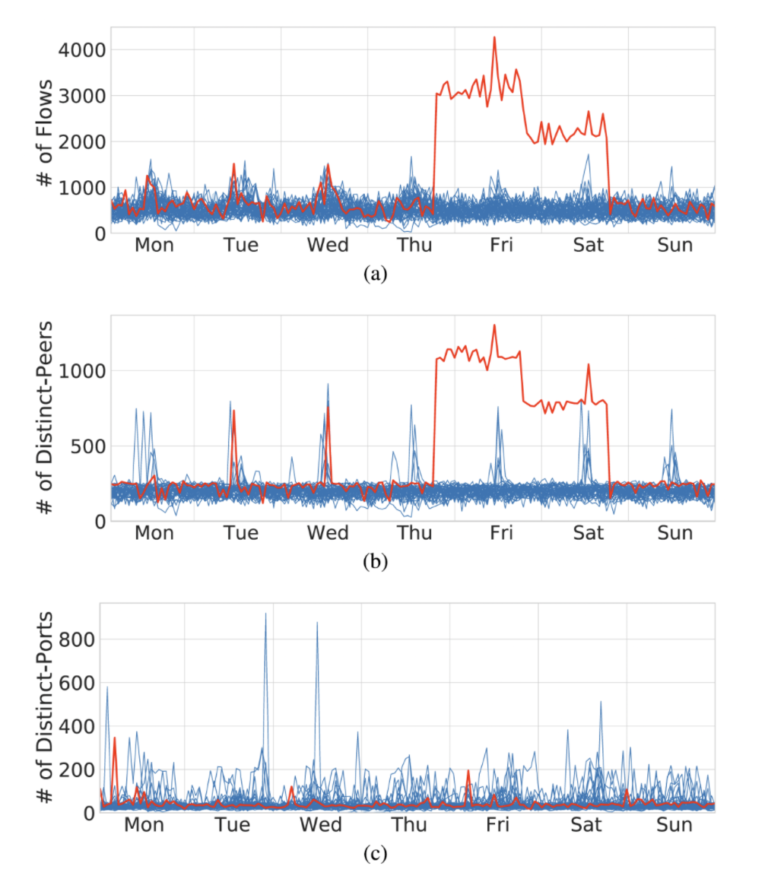
CONCLUSION
The examples shown in the blog provide only a glimpse of the possibilities of modeling the host behavior based on the data captured from network traffic. The host behavior modeling can be efficiently applied in various areas of network management, such as network segmentation, network policies settings, or even cybersecurity incident prioritization. All examples presented in the blog are explained and described in detail in [2], along with an open-source dataset of one-year host behavior data available on a public repository.
[1]: R. Hofstede et al., “Flow Monitoring Explained: From Packet Capture to Data Analysis With NetFlow and IPFIX,” in IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 2037-2064, Fourthquarter 2014, doi: 10.1109/COMST.2014.2321898.
[2]: T. Jirsik and P. Velan, “Host Behavior in Computer Network: One-Year Study,” in IEEE Transactions on Network and Service Management, vol. 18, no. 1, pp. 822-838, March 2021, doi: 10.1109/TNSM.2020.3036528.
Tomas Jirsik received the Ph.D. degree in informatics from the Faculty of Informatics, Masaryk University, Czech Republic. He is currently a Senior Researcher with the Institute of Computer Science, Masaryk University and a Member of the Computer Security Incident Response Team, Masaryk University, where he leads national and international research projects on cybersecurity. His research focus lies on the network traffic analysis with a specialization in host profiling. His research further includes network segmentation approaches via machine learning and host fingerprinting in network traffic.